
RFID タグはどのようにデータを保存するのでしょうか?
目次
導入
このプロセスを理解することは単なる学術的な問題ではない。スマートサプライチェーンを設計するエンジニア、RFID統合アプリを開発する開発者、大規模な資産追跡を監督するIT管理者にとって、RFIDのメモリ、データ符号化、セキュリティプロトコルの基盤となる仕組みは、性能、相互運用性、データ完全性にとって極めて重要である。.

RFID とは何ですか? どのように機能しますか?
RFIDとは何か?
RFID(無線周波数識別)は、電磁場を用いて物体を自動的に識別・追跡する無線技術である。バーコードとは異なり、RFIDは直接の視線が必要なく、より多くのデータをタグに直接保存できる。.
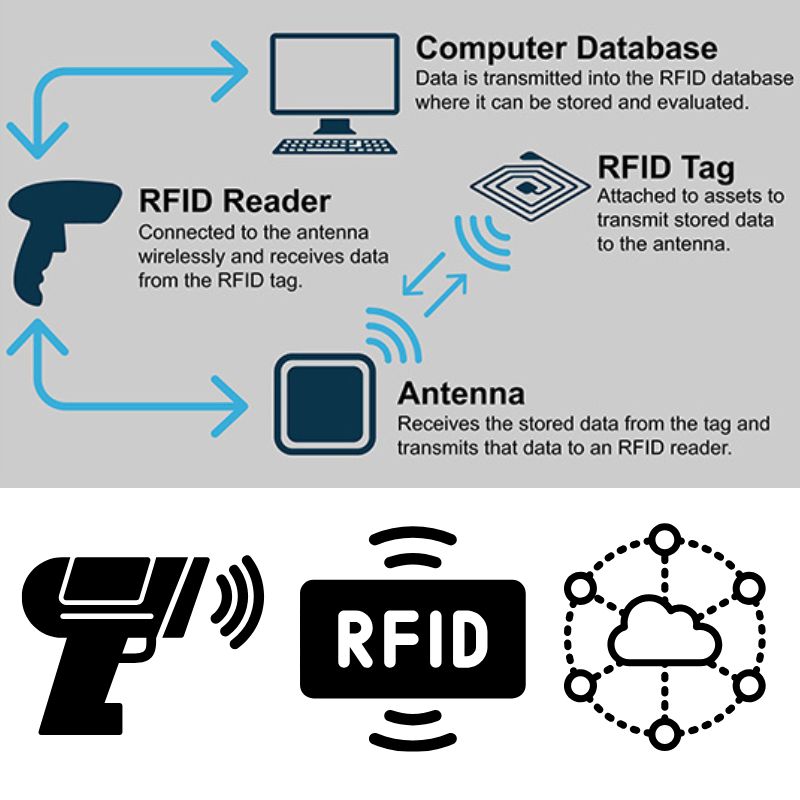
RFIDシステムの主要構成要素
データ伝送の仕組み
RFIDリーダーが無線周波数信号を発すると、タグのアンテナがこれを捕捉し、チップに電力を供給する(パッシブ型の場合)。その後、チップは変調を行い、保存されたデータをリーダーに送信する。この通信は周波数によって異なる:
- LF(低周波数):短距離、動物追跡に適している。.
- HF(高周波):NFCやスマートカードで一般的。.
- UHF(超高周波):長距離通信、高速読み取り速度 – 物流に最適。.
エンジニアリングのヒント:パッシブUHFタグは、低コストで数メートルまで通信可能なため、産業用サプライチェーンで最も一般的に使用されています。.
RFIDタグプログラミング入門ガイド
RFIDタグのプログラミングは、製品データのカスタマイズから安全なアクセス制御の実現まで、強力な機能を引き出すことができます。多くのツールや手法が存在しますが、具体的な方法はタグの種類、周波数、および用途によって異なります。.
現在、RFIDタグを安全かつ効果的にプログラミングするための検証済みコード例と実践的な手順解説を作成中です。このセクションにはまもなく以下が含まれます:
- ArduinoとRFIDモジュールを組み合わせた実践チュートリアル.
- TagWriter(Android)を使用したデータのエンコーディング NFC対応タグ.
- 企業向けアプリケーションにおけるRFID SDKおよびデスクトップライターの活用.
- 適切なメモリ形式(ASCII、HEX、EPC)の選択に関するヒント.
今すぐ始めたいですか?その間、以下のリソースをぜひご覧ください:
- NXP TagWriter アプリ– Android向けNFCエンコーディング
- MFRC522 Arduinoライブラリ(GitHub)– オープンソースRFIDリーダーライブラリ
- 特定のリーダーモデル向けの[ハードウェアベンダーのSDKまたは開発者ツール]
RFIDタグへのデータ書き込みや互換性のあるツールの選択でお困りですか? 技術チームにお問い合わせください をご覧ください。
RFIDタグが内部でデータを保存する方法
RFIDタグの本質は、特定のメモリバンクを備えた微小な記憶装置である。どのようなデータを、どれだけの量を保存するかを計画する際には、内部メモリのレイアウトを理解することが極めて重要である。.
RFIDタグのメモリの種類
- ROM(読み取り専用メモリ):製造時に書き込まれたデータ。変更することはできません。.
- EEPROM(電気的に消去可能):書き換え可能。現代のRFIDで最も一般的に使用される。.
- RAM: 一時的な記憶装置。アクティブなトランザクション中に頻繁に使用される。.
一般的なメモリの種類
- 読み取り専用 (RO): 変更不可。固定IDに使用されます。.
- 読み取り/書き込み (RW): 互換性のあるリーダーで変更可能。.
- WORM(書き込み一回、読み取り複数回):一度プログラムされると、データはロックされる。.
EPCglobal Gen2タグ(UHF)のメモリバンク
| メモリーバンク | 目次 | 書き込み可能? |
|---|---|---|
| 電子計算機 | 製品ID(96~128ビットが一般的) | ✅ |
| TID | 固有のタグ/チップ識別子 | ❌ |
| ユーザーメモリ | アプリケーション固有のデータ | ✅ |
| 予約済み | アクセス/キルコマンドのパスワード | ✅ (制限付き) |
ベストプラクティス:SKUや製品識別子にはEPCを使用し、タイムスタンプ、ロット番号、物流メタデータなどの追加データにはユーザーメモリを使用してください。.
ビットおよびブロックのフォーマット
- メモリはブロック(16ビットまたは32ビット)に分割される。.
- 各ブロックは個別にアドレス指定できます。.
- データエンコーディングはブロックサイズとタグ仕様を遵守しなければならない。.
例:512ビットのユーザーメモリを持つタグには、エンコード用に64バイトが利用可能です。データ構造をそれに応じて計画してください。.
RFIDタグ上のデータはどれほど安全か?
RFID技術がサプライチェーンや消費財に統合されるにつれ、データセキュリティが最重要課題となっている。RFIDタグがデータを保護する一方で、時にデータを晒す仕組みを理解することは、安全な導入に不可欠である。.
RFIDタグはハッキングされる可能性があるか?
はい——ただし状況が重要です。基本的な低コストタグは複製やスキミングが可能ですが、現代のRFIDシステムの多くは、アクセス制御や暗号化を含む複数のセキュリティ層を実装しています。.
RFIDタグのセキュリティ機構
| セキュリティ機能 | 説明 | 保護レベル |
|---|---|---|
| パスワード保護 | 不正な読み取り/書き込みをブロックする | 中くらい |
| アクセス制御ビット | メモリバンクごとに読み取り/書き込み権限を定義する | 高い |
| 暗号化(AES、DES) | 高セキュリティタグ(例:銀行、アクセス制御)に使用される | 非常に高い |
| キルコマンド | タグを恒久的に無効化し、悪用を防ぐ | 文脈依存の |
一般的な脆弱性
- 盗聴:攻撃者がタグリーダー通信を傍受する。.
- クローン:タグデータを別のタグにコピーすること。.
- リプレイ攻撃:傍受した通信データを再利用すること。.
安全なRFID導入のためのベストプラクティス
- 機密データにはパスワード保護または暗号化されたタグを使用してください。.
- 機密情報をタグに直接保存しないでください。参照情報またはIDのみを保存してください。.
- タグデータを検証するための安全なバックエンドデータベースを実装する。.
- 機密性の高い状況では、使用後にタグを保護または無効化してください。.
RFIDタグはどれだけのデータを保存できますか?
エンジニアが最もよく尋ねる質問の一つは:
“「RFIDタグにはどれだけのデータを保存できますか?」”
代表的なRFIDメモリ容量
| タグタイプ | メモリ範囲 | 使用事例 |
|---|---|---|
| 低周波(LF) | 64~256ビット | 動物識別タグ、アクセスカード |
| 高周波(HF/NFC) | 128~4,096ビット | スマートカード、在庫 |
| 超高周波(UHF) | 96–8,192ビット | 物流、産業追跡 |
| アクティブRFID | 32キロバイト以上 | センサーデータ、大容量ペイロード |
容量に影響を与える要因
- タグ頻度とチップモデル。.
- 暗号化またはチェックサムデータの使用。.
- アプリケーションタイプ(例:EPCエンコーディング対ユーザー定義).
一般的にどのようなデータが保存されますか?
- 製品識別子(EPC)
- バッチ番号またはロット番号
- タイムスタンプ
- アクティブタグ内のセンサーデータ(温度、圧力)
ヒント:タグには必要な最小限のデータのみを保存し、詳細については外部データベースにリンクします。これによりメモリ要件が削減され、パフォーマンスが向上します。.
パッシブ型とアクティブ型RFID:データ保存能力の比較
パッシブ型とアクティブ型のRFIDの選択は、コスト、データ容量、通信距離に影響を与える。.
| 特徴 | パッシブRFID | アクティブRFID |
|---|---|---|
| 電源 | Powered by reader | 内蔵バッテリー |
| データ容量 | 96–8,192ビット | 32キロバイト以上 |
| 範囲 | 最大10メートル | 最大100メートル |
| 寿命 | 無制限(バッテリー不要) | バッテリー寿命によって制限される |
| 料金 | <$0.10 1タグあたり | $10–$50(タグあたり) |
どちらを選ぶべきか?
- パッシブタグ:在庫管理、小売、アクセス制御に最適。.
- アクティブタグ:リアルタイム資産追跡、物流、IoTセンサーに最適。.
実例 — RFIDタグにはどのようなデータが保存されているのか?
実際の産業分野におけるRFIDデータストレージの仕組みを見てみましょう。.
小売業において
- 製品識別子(EPC)
- 価格、SKU、ロット番号
- 棚位置またはカテゴリーデータ
ヘルスケア
- 患者ID
- 薬剤投与量情報
- 機器追跡
物流において
- 出荷ID、タイムスタンプ
- コンテナコード
- ルートとチェックポイントの追跡
動物追跡において
- 品種識別番号、ワクチン接種記録
- GPSまたは位置識別子(アクティブタグ内)
プロの知見:ほとんどの企業システムでは、タグIDをクラウドデータベース(ERP、WMS)に紐づけることで、タグ自体に大規模なデータセットを保存する必要性を低減しています。.
RFIDタグへのデータ書き込み方法(エンコーディングプロセス)
ハードウェア要件
- RFIDライターまたはリーダライタモジュール
- 互換性のあるソフトウェア(TagWriter、Arduino IDE、またはSDK)
- RFID対応タグ
典型的なエンコーディングワークフロー
- ライターをシステムまたはマイクロコントローラに接続してください。.
- タグの種類と周波数(LF、HF、UHF)を選択してください。.
- データ形式を選択してください(EPC、HEX、またはASCII)。.
- ソフトウェアコマンドを使用してタグにデータを書き込む。.
- 読み取り関数を使用してデータを検証する。.
一般的なエンコーディング形式
| 形式 | 例 | 使用事例 |
|---|---|---|
| EPC(96ビット) | 300833B2DDD9014000000001 | 製品ID |
| HEX | 0xA1B2C3D4 | バイナリデータストレージ |
| ASCII | “「ITEM00123」” | 読み取り可能な文字列 |
産業用エンコーダーをお探しですか?当社の製品をご覧ください RFIDライターキット UHFおよびNFCシステム向け。.
RFID vs. バーコード vs. NFC:データ保存容量の比較
| 特徴 | RFID | バーコード | 非対称 |
|---|---|---|---|
| データ容量 | 64ビット–32キロバイト | 12~20文字 | 最大4KB |
| 読み取り範囲 | 1–100 m | 0.2~1 m | 0-10cm |
| 書き換え可能? | はい | いいえ | はい |
| 同時読み取り | 数百のタグ | 一つずつ | 一つずつ |
| 耐久性 | 高い | 低い | 中くらい |
重要なポイント
- RFID:高速・大容量データ環境において最適。.
- バーコード:静的IDにはシンプルで安価。.
- NFC:安全な短距離通信(例:決済)に最適。.
バーコードからRFIDへのアップグレードをお考えですか? 無料導入見積もりを取得する。.
RFIDデータストレージに関するよくある質問
RFIDタグは書き換え可能ですか?
はい — ほとんどのHFおよびUHFタグは、メモリの劣化が発生するまで複数の書き込みサイクルをサポートします。.
RFIDタグ上のデータはどのくらい残りますか?
チップの品質により、パッシブタグは最大10年以上持続します。.
RFIDデータは暗号化されていますか?
一部のタグはAES/DES暗号化をサポートし、他のタグはパスワード保護に依存します。.
スマートフォンでRFIDタグをプログラミングできますか?
はい、それらがNFC対応(13.56 MHz)であり、お使いのスマートフォンにNFCリーダーが搭載されている場合です。.
RFIDタグへの書き込みにはどのソフトウェアが使用されますか?
TagWriter、Arduino IDE(ライブラリ付き)、またはメーカーのSDK。.
RFIDデータストレージの未来
RFIDの未来は、IoTとAIの交差点にある。タグは単にデータを保存するだけでなく、クラウドシステムやセンサーと能動的に通信するようになる。.
新興イノベーション
- マイクロEEPROM技術によるメモリ密度の向上
- 温度または動作データを保存する統合センサー
- AI駆動型RFID分析による意思決定の自動化
- ブロックチェーンを活用した製品真正性のトレーサビリティ
結論:まとめると
RFIDタグは小型でありながら強力なデータキャリアであり、現代の自動化の基盤を成す。.
基本的な記憶構造から高度な暗号化まで、RFIDタグがデータを保存・送信する仕組みを理解することで、エンジニア、開発者、企業はよりスマートで安全なシステムを構築できるようになります。.
主なポイント:
- 範囲、容量、用途に基づいてタグの種類を選択してください。.
- 機密データには、安全なパスワード保護された暗号化を使用してください。.
- 拡張性を確保するため、RFIDをバックエンドシステムと統合する。.
RFIDシステムの設計やプログラミングでお困りですか?
チームへのお問い合わせ カスタムRFIDソリューション、ハードウェア調達、および導入支援のため。.

レイ・ジョウ
この記事は、RFID技術の専門家であり、10年以上の業界経験を持つRay Zhouが執筆した。
コメント
人気商品

物流におけるRFID:RFID誤配送とRFIDラベル故障の解消方法
物流におけるRFIDは、単にプロセスを迅速化するツール以上の存在である。現代のサプライチェーンが機能する上で、その重要な要素となっている。.
RFID廃棄物管理とは何か
想像してみてください。街中のゴミ箱がすべて「話す」街を――文字通りではなく――小さなチップを通じて、満杯になった時、空になった時、そしてどこへ運ばれたかをシステムに伝えるのです。それが今日のRFID廃棄物管理の仕組みです。.

ボルトシールとその用途とは?| 完全ガイド
世界的な貿易と物流において、ボルトシールは貨物のセキュリティとコンプライアンスを確保する上で重要な役割を果たしています。これらの小型で強力なデバイスは、タンパーエビデント機構で輸送コンテナ、トレーラー、貨物ドアをロックするように設計されています。

RFIDカードプロテクターとは?メリット、使用例、購入ガイド
RFID(Radio Frequency Identification)テクノロジーは、クレジットカード、IDバッジ、定期券、ホテルのルームキーなど、あらゆるところに浸透している。RFIDはスピードと利便性を提供する一方で、「スキミング」と呼ばれる新たなデジタル窃盗への扉も開いている。そこでRFIDカードプロテクターの出番です。

イベント用RFIDリストバンド:主催者向け一括購入ガイド
イベント用RFIDリストバンドは、コンサート、フェスティバル、スポーツ会場などで、迅速な入場、不正防止、キャッシュレス決済を必要とする主催者にとって、最適なソリューションになりつつあります。紙のチケットやQRコードとは異なり、これらのスマートリストバンドは埋め込みチップを使用し、アクセスを合理化し、取引を安全にし、ゲストの体験を向上させます。

フロントガラス上のRFIDタグが車両入退場管理と料金システムを改善する方法
ペースの速い今日の世界では、車両識別は迅速、安全、非接触である必要があります。フロントガラス上のRFIDタグは、まさにそれを提供します-車両を止めることなく、料金徴収、駐車、ゲートアクセスを管理する信頼性の高い方法です。
タグ
関連ブログ

物流におけるRFID:RFID誤配送とRFIDラベル故障の解消方法
物流におけるRFIDは、単にプロセスを迅速化するツール以上の存在である。現代のサプライチェーンが機能する上で、その重要な要素となっている。.

RFID廃棄物管理とは何か
想像してみてください。街中のゴミ箱がすべて「話す」街を――文字通りではなく――小さなチップを通じて、満杯になった時、空になった時、そしてどこへ運ばれたかをシステムに伝えるのです。それが今日のRFID廃棄物管理の仕組みです。.

ボルトシールとその用途とは?| 完全ガイド
世界的な貿易と物流において、ボルトシールは貨物のセキュリティとコンプライアンスを確保する上で重要な役割を果たしています。これらの小型で強力なデバイスは、タンパーエビデント機構で輸送コンテナ、トレーラー、貨物ドアをロックするように設計されています。




